 FEATURED
FEATUREDPETER WELCHER | Solutions Architect
For an overview of information and additional context surrounding Elisity, read the prior blog articles as follows:
I like Elisity’s identity-based campus security approach, especially for small to medium sites that need less complexity in a targeted approach, and especially for medical/industrial sites grappling with OT/IOT/IIOT device security. Currently, Elisity requires you to have recent Cisco Catalyst switches.
This blog covers new features in the Elisity 15.2 to 15.4 code releases.
Just updated in 15.5.0: Elisity now supports Arista
I previously blogged about other approaches from Cisco and Juniper that address the IoT distributed security challenges by providing for much larger firewall deployments (physical or virtual). I mention this because this confirms the market need that Elisity addresses.
Background: About Elisity
Elisity is a cybersecurity firm in the Zero Trust space (Identity Based Micro-Segmentation) that focuses on campus/industrial/medical network segmentation.
While Elisity provides the ability to simplify segmentation for any campus network at scale, their special niche is providing the ability to micro-segment OT/IOT/IIOT devices in networks.
Their big selling point is Time To Value: no impact deployment with initial results within about 2 weeks.
This is a major requirement for hospital, medical, and industrial networks, particularly because medical or other IOT devices may not be running solidly hardened code and because they are proliferating in large numbers, often without central IT or Security team awareness, control, or visibility. Additional security is needed now (or soon), and due to thin staffing, it must be easy to deploy.
The challenge is that IoT devices, including medical patient monitors and environmental sensors, may be ubiquitous. Isolating them for security means putting lots of firewalls (physical or virtual) in the network, potentially in or attached to many campus switches. Large numbers, high costs, high admin burden. Alternatives are needed.
Noteworthy: Elisity’s approach is simpler and more affordable as long as you need segmentation but no other firewall services such as VPN, stateful enforcement, or traffic inspection.
Of course, this is always the key question: what are your requirements, what problem(s) are you trying to solve? Elisity provides simplicity, rapid deployment, and no new devices or topology changes.
This blog discusses useful new features in the Elisity 15.2 to 15.4 releases.
How Elisity Operates
Elisity provides cloud-based management. Local control points or agents (“Virtual Edges/VEs”) run in the network as containers on campus switches or on local servers/VM hosts.
The VEs stage policy deployment from the cloud control point, pushing policy into the locally controlled switches (“Virtual Edge Nodes”). They also pass identity and context information upstream to the cloud controller.
For more details and some images, please see my prior Elisity blogs, in the Links section below.
What’s New in 15.2
Version 15.2 is heralded as a major update, including a complete overhaul of the identity engine, and adding new functionality.
Specific new items of interest:
- IdentityGraph
- Bulk Policy Actions
- Multi-Select Policy Creation
IdentityGraph is the core of Elisity’s Identity Engine. It is a mapping service that builds a graph of users, devices, and applications as their identity attributes, traffic patterns, and relationships. This facilitates user creation of asset groups and policies. It connects with other platforms such as Medigate, Claroty, ServiceNow, and Tenable.
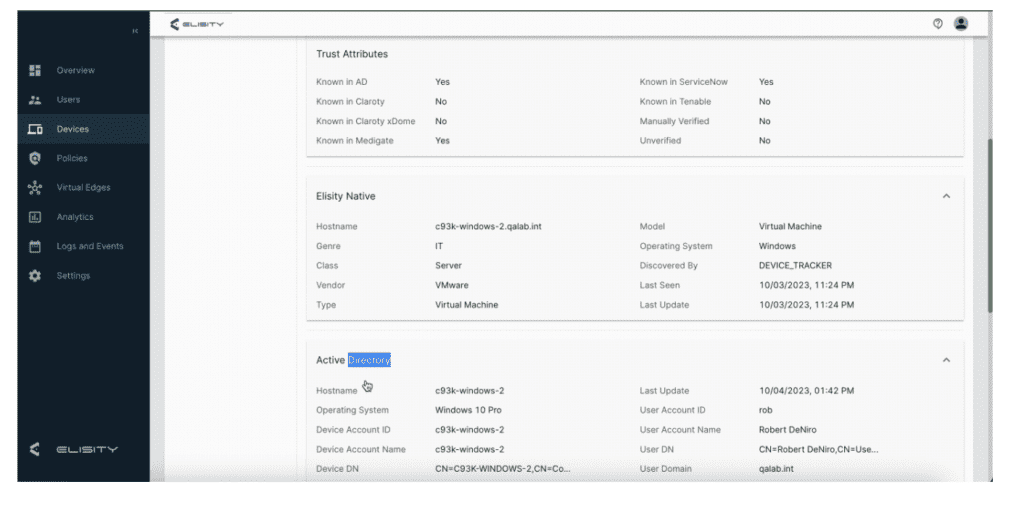
The overall purpose is to enrich data for greater device attribute accuracy.
As noted in prior blogs, the Elisity traffic matrix helps visualize traffic to/from known assets and helps understand the potential or actual impact of policies.
Bulk Policy Actions lets the administrator work with multiple policies at one time, e.g., activating or simulating them, or deleting them.
Multi-Select Policy Creation lets you deploy a single policy across multiple policy groups at one time. This is typically done within the Policy Matrix (see prior blogs), where you can select multiple cells in the matrix and apply the policy to them.
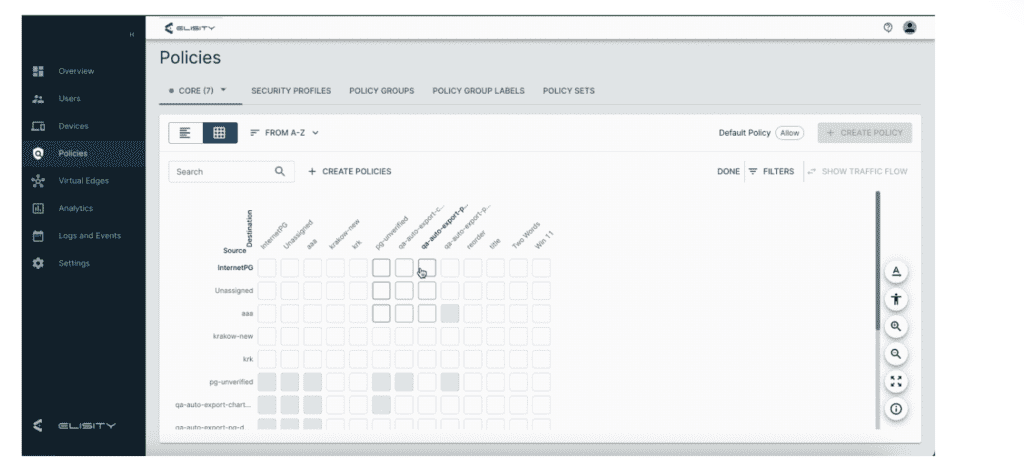
Other new features:
- Tenable connector pairs Elisity’s rapid device discovery with Tenable’s device identification, providing enriched device attributes as well as acting as an additional trust attribute for Elisity. That is, Elisity can trust the device based on its being known to Tenable.
- Claroty xDome Connector: Similar features include enriched device attributes and acts as an additional trust attribute.
- Medigate Connector and ServiceNow updates: ditto. ServiceNew CMDB attributes can now be used as match criteria.
- Active Directory update and changes. Devices are no longer imported from AD. Instead, AD now provides enriched device attributes and a trust attribute, as above.
- Device labels: user-defined labels provide a way to differentiate (similar) devices.
What’s New in 15.3 and 15.4
Release 15.3 adds more sophisticated filter creation convenience and features, e.g., multiple IPs or subnets at one time when creating a filter, “unverified” as an attribute for match criteria, and risk score matching in policy groups. Also, policy per-rule syslog logging is available.
Release 15.4 adds a Palo Alto IOT Security Connector. Device attributes learned via connectors can now be manually refreshed as desired, rather than waiting out a 24-hour automated refresh. 15.4 also adds new (beta) analytics for network traffic: a Sankey chart view and a flow table view.
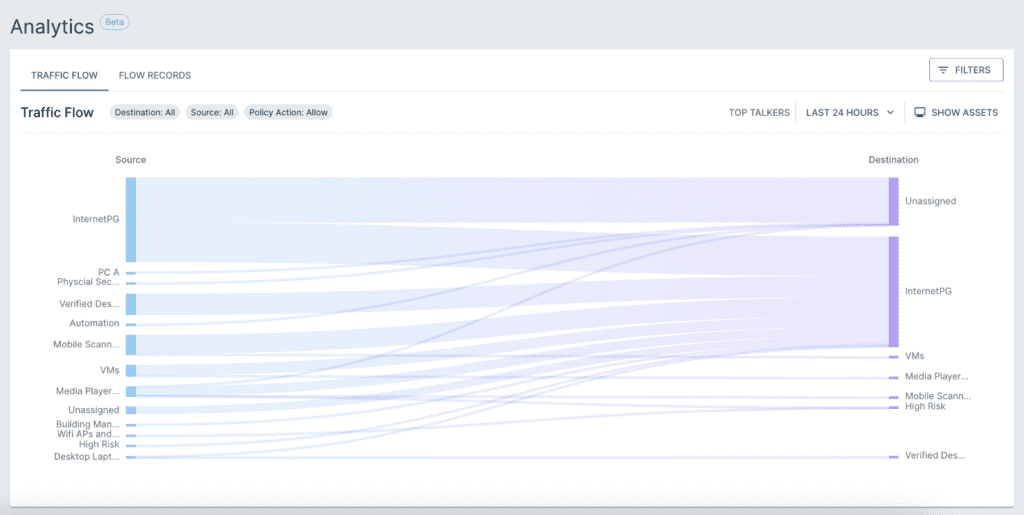
In addition, the control plane between the Virtual Edges (VEs) and the Cloud Control Center now uses DTLS 1.3, for significant performance and reliability improvement of control communications.
Update to the update: follow the Release Notes link below for updates about additional new features in releases 15.4.1, .2, .3, .4, and .5 (and any other updates that come out before this blog gets posted!)
Links
Elisity content about 15.2 (and general/later release notes):
- LinkedIn post about Elisity’s new features in 15.2: https://www.linkedin.com/posts/danayanch_elisity-releases-version-152-activity-7118730259297931264-OEXg
- Elisity blog about the 15.2 features: https://blog.elisity.com/elisity-releases-version-15.2
- Elisity Release Notes: https://support.elisity.com/hc/en-us/sections/16079687178772-Cloud-Control-Center-Release-Notes
- Video presentation for ONUG about Elisity: https://www.dropbox.com/scl/fi/3rka3vrcegxg9vkvz8nsi/Dynamic-Edge-Segmentation-with-Elisity-FINAL.MP4?rlkey=6qxmkv09daia5cniz2smfzd9g&dl=0
Conclusion
Elisity continues to add useful functionality to help secure campus networks, with a special focus on IOT (and OT, IIOT) device segmentation.
Ease of use provides greater ability to not just segment off IoT devices but to segment different sets of devices and provide device-type specific access controls to those devices (e.g., access to/from a server that manages that group of devices).








































