 FEATURED
FEATUREDPETER WELCHER | Solutions Architect
The founders of Graphiant built Viptela, a company that Cisco acquired in 2017. Taking the lessons they learned, Graphiant developers improved their approach to typical SD-WAN, avoiding encrypted tunneling spaghetti.
This blog updates my prior blogs with new links to improved information about their work.
Graphiant exposes a lot of technical detail in their presentations, so this article is a summary of their process. For a more granular view of their work, read the tech whitepaper linked below or watch the videos.
About Graphiant
Graphiant has an interesting technical play. Graphiant rethinks SD-WAN and, to some extent, provider-based MPLS. They anticipate a lot of edge network growth, with sites as data generators, so scaling is a prominent factor to consider. Agility will also be needed.
Benefits to Graphiant:
- A significantly more cost-effective and agile approach.
- It can run as virtual edge, hardware edge, or cloud edge – there are performance considerations regarding virtual devices, but this facilitates quickly standing up a new site.
- Competes with SD-WAN: avoids many VPN/tunnels, supports segmentation and segment connectivity controls.
- Smarter secure forwarding, using label-based forwarding but simplifying provider MPLS’s complexity and provisioning time.
- Stateless core provides transit between edge sites and gateways without session awareness or repeated decrypt/encrypt.
- Cloud-management portal. Graphiant provides secure connectivity while you orchestrate the routing logic, segmentation, and policy.
- Edge devices include router + firewall functionality, including NAT (Note: I have not yet seen details regarding the firewall capabilities).
- Can work with SSE (Security Service Edge) partners.
For information on how Graphiant works, see my prior technical blog (link below) or the recent Graphiant Technical Whitepaper (link below).
One key nifty technical aspect is that Graphiant provides edge-to-edge payload encryption with crypto-signed secure edge connections. This avoids the need for any middle decryption/re-encryption inefficiency.
You would use Graphiant gateways to connect to cloud, SaaS, etc. (sites outside the system).
From various sources, I gather they have been building out an international presence based on a growing number of cloud and colo presences with high-speed links between. Internationally, they offer service provider partners a chance to connect with customers globally. Within the U.S., Graphiant has been expanding based on Equinix colos and backbone capacity.
Another key point is that Graphiant’s approach uses VRF routing and SR tags in its core. You ask, “So what?” Well, that sounds less complex than the typical Service Provider MPLS device. And a manual provisioning of circuits. So rapid deployment for new customers – the gating factor seems like site installation of the Graphiant edge devices – which I view as Provider Edge devices but at customer premises.
Consuming Graphiant
Graphiant provides the core network.
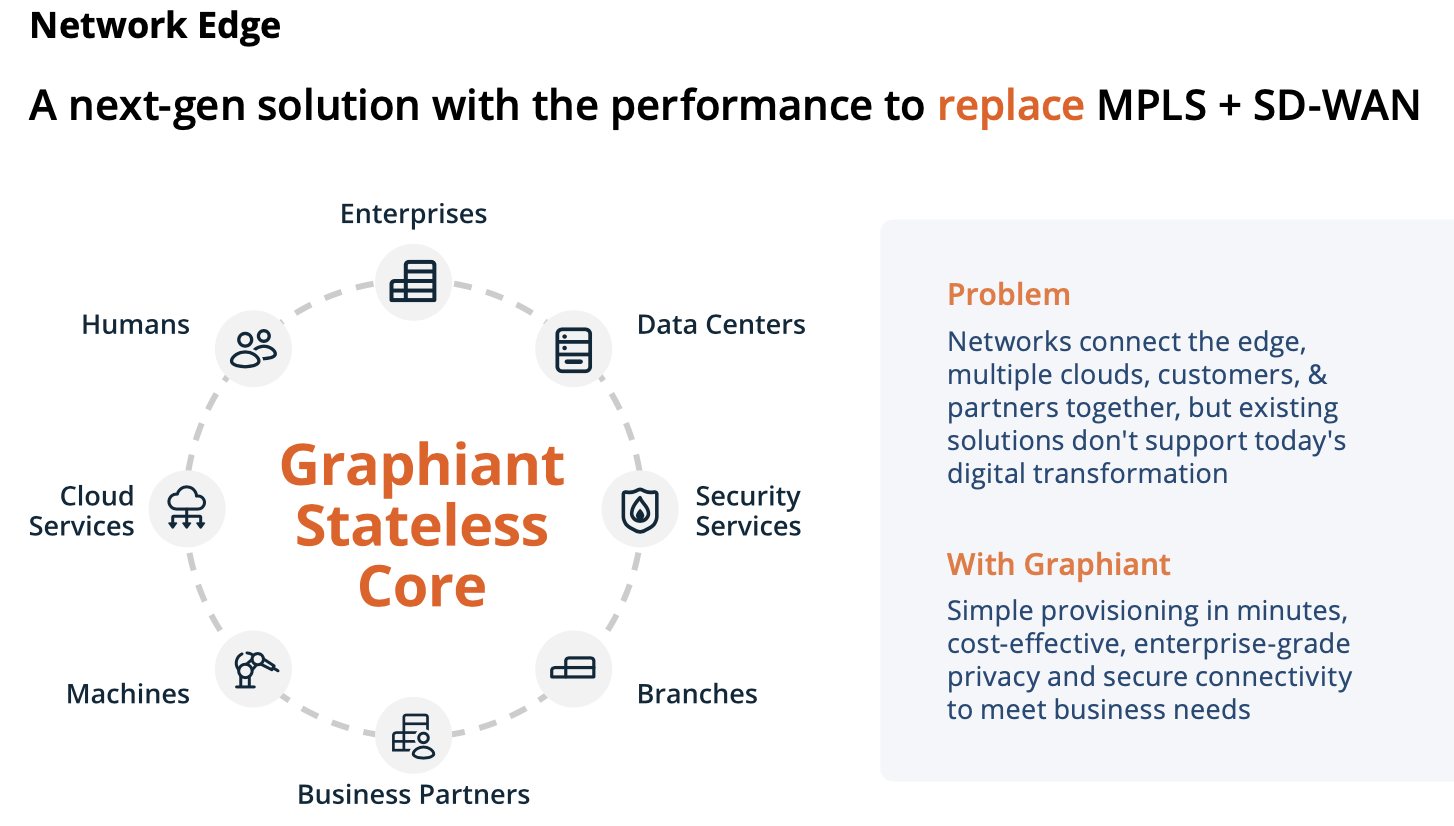
Partners (initially WWT) deploy Graphiant routers at customer sites and link them to the core. Customers (or presumably Graphiant partners) use the cloud-based controller to set up the desired connectivity.
Gateways provide connectivity (as a service) to Cloud and SaaS providers.
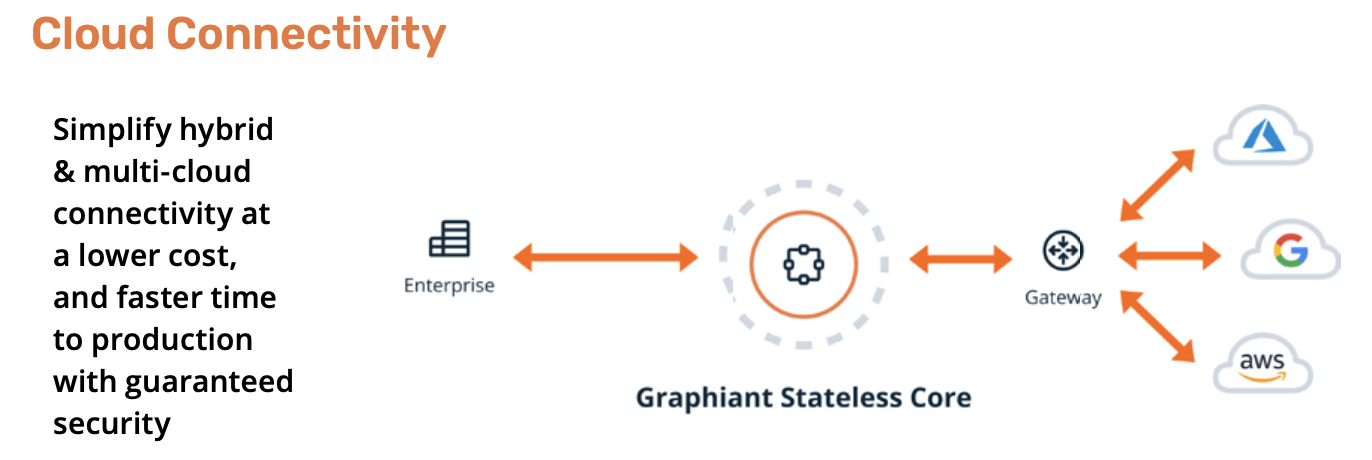
Reading between the lines, I hypothesize that this could be deployed faster than the typical MPLS deployment, while leaving the customer with control over the part they care about: the connectivity rules and routing.
Securing Graphiant
Graphiant has segmentation and connectivity control capabilities, but the language surrounding these capabilities is vague. Some of it sounds like firewalling rules, but other parts of the verbiage sound more like routing, as in, traffic cannot be forwarded between A and B in either direction. Some of it sounds like tag filtering based on GUI.
The lack of detail may indicate a work in progress, or that Graphiant has not gotten around to documenting this aspect — or that I just have not stumbled across the right documentation yet.
Links
Graphiant: https://graphiant.com
Graphiant Technical Whitepaper (HOW IT WORKS!): https://graphiant.com/wp-content/uploads/2023/08/Graphiant-Technical-Whitepaper.pdf (open download, no form to fill out and trigger a salesperson call!)
My prior blog from the Graphiant launch: https://www.linkedin.com/pulse/nfd29-graphiant-peter-welcher/
Network Field Day (NFD) 33, Fall, 2023: FIVE videos, some title overlaps with ONUG: https://techfieldday.com/appearance/graphiant-presents-at-networking-field-day-33/
They include:
- Graphiant Intro and Rise of the Business Internet presentation: https://youtu.be/6PYpQPl-ahc
- Graphiant Service and Use Cases: https://youtu.be/9ZgdDf8AahM
- Deep Dive on Network Edge Service (Automated Orchestration and Bring Up): https://youtu.be/ff-lcr5cvug
- Graphiant Gateway Service: https://youtu.be/j0_fNsQyRow
- Cloud Gateway Services with Demo of OCI and Jumbo Frames: https://youtu.be/vHXYhX0tM0g
Tim Bertino’s LinkedIn blog based on NFD33: https://www.linkedin.com/pulse/new-approach-private-connectivity-graphiant-tim-bertino-2cshc/
Prior TFD coverage: https://techfieldday.com/companies/graphiant/
Graphiant presented twice at ONUG, Fall, 2023. Titles:
- The Rise of the Business Internet – Sponsored by Graphiant.
- Graphiant Proof of Concept: Leverage the Power of Jumbo Frames to Accelerate Your Cloud Networks.
ONUG survey, Fall, 2023 re new use cases for Enterprise Networking: https://graphiant.com/onug-survey/
ONUG, Spring 2023: https://onug.net/events/graphiant-proof-of-concept-connect-the-edge-with-the-graphiant-solution/
Conclusion
Networking comes with a constant tension between simplicity, functionality, and scale. Time to function, or agility, is also a concern.
Graphiant has rethought the WAN network with those considerations in mind. They have a pre-built high-speed core network you can use as a service. The cloud controller provides simple provisioning and onboarding of new edge devices. Segmentation helps you control where specific traffic goes. You control that through the portal—no waiting for an MPLS provider to provision a new connection.











































