 FEATURED
FEATUREDPETER WELCHER | Solutions Architect
About Mammoth Cyber
Mammoth Cyber exists in the ZTNA space. However, their product does NOT use an agent, per se.
Instead, they have a modified version of Chromium with a central Cloud-based controller: the “Enterprise Access Browser” (“EAB”). The controller (“Mammoth Admin Console”) authenticates users, informs the modified browser component about what the user can access, and controls potential data export, including screen capture, upload/download, etc. In short, “Conditional Access with Centrally Managed Access Control”.
Images are watermarked to deter data capture via photographing the screen.
In effect, the agent is built into the modified web browser.
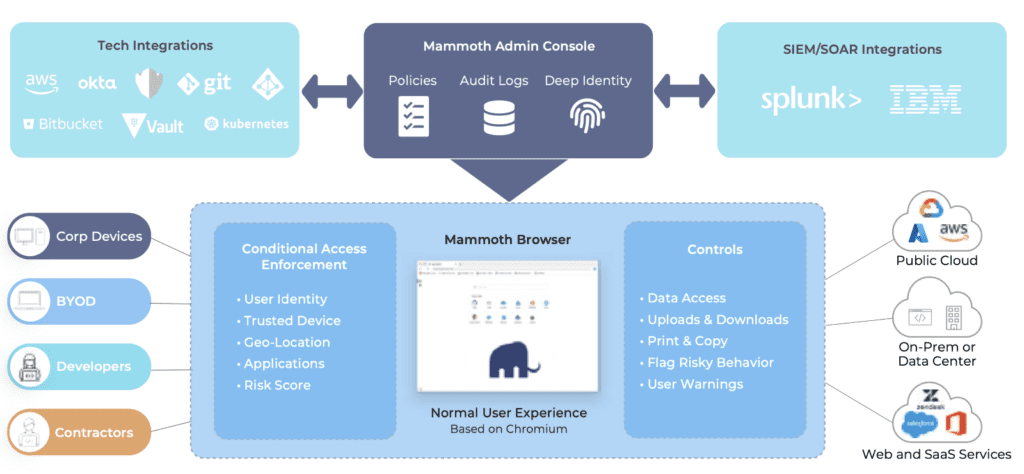
The primary use case for this is remote employees, contractors, partners, and BYOD users. This is an interesting niche: users that fall outside of traditional network-based security but for whom agent-based ZTNA may not be the best fit.
This market also includes sites currently using VDI or VPN to control such access. In general, direct web access should provide a significantly better user experience than VDI, at a lower cost.
I imagine that for organizations with internal staff that only need access to web-based tools, it might provide a simplified way to handle device provisioning and role-based access controls.
Given that Chromebook computers have been a workable solution for many for years, there may well be a large number of enterprise users for whom browser-based access suffices.
The controller integrates with Okta, Azure AD, and other products for user ID and authentication. This is a moving target as they add support for other ID sources.
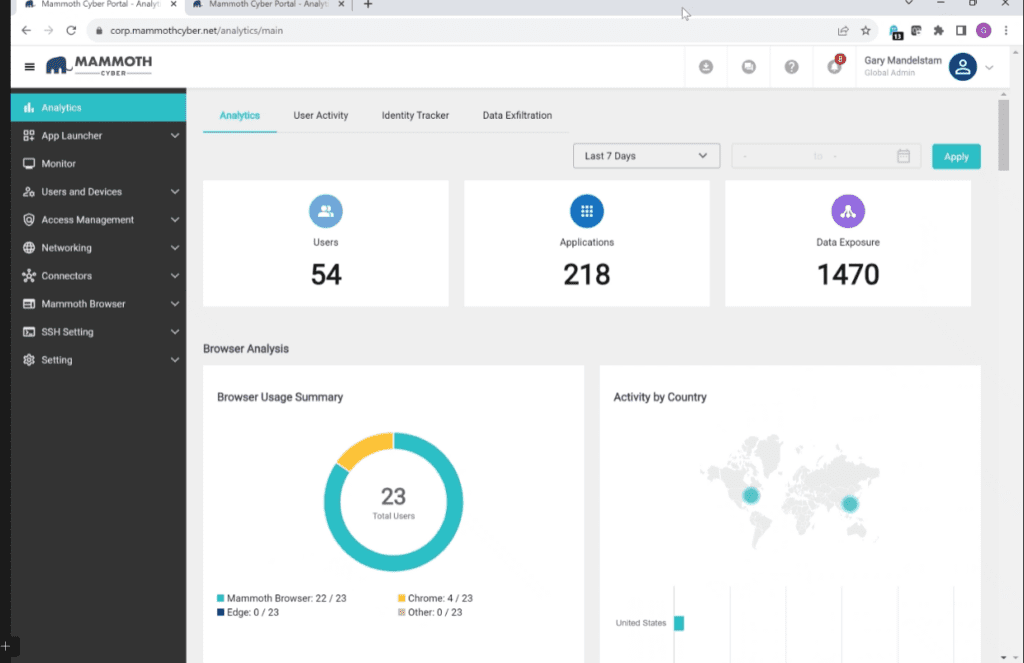
The controller logs and provides visibility into who accessed what and when. It knows the user ID and applications accessed and what permissions were assigned. It integrates with Splunk and IBM for SIEM functionality. If the administrator chooses, exported data can be logged.
The following screen capture shows the controller admin and analytics tool.
Access for Developers
Mammoth Cyber’s solution also supports solid performance for development/engineering users by enabling a secure use of local resources for SSH, RDP, Git, Kubernetes, and Database access. I believe these run in a local container (the presentation only lightly touched on this, and I cannot confirm it online).
Setup Process
Deploying Mammoth Cyber looks fairly straightforward:
- Integrate with IDP for user authentication.
- Configure applications allowed and access rules.
- Deploy “Service Edge” for secure connection to data center applications (and public cloud apps). This introduces an enforcement point in the data center to simplify ACL controls. I was unable to find more information.
- Use the EAB to connect to applications.
There are two modes of operation:
- Auto-Launch Seamless: users are redirected to Mammoth for enterprise apps.
- Mandated Browser: for third-party unmanaged devices, the browser acts as a lightweight virtual desktop for access to internal and cloud-based enterprise apps.
Links
Conclusion
Mammoth Cyber looks like a low admin overhead and performant way to control access to enterprise applications.











































